Red Herring have released their Top Security trends for 2006, with the headline "Security threats will become more sophisticated in 2006, keeping security startups and their customers on their toes."
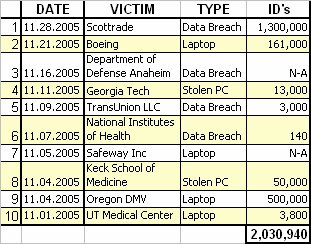
Data theft wasn’t the only danger in 2005. An Internet worm, Zotob, infected computers at media companies like CNN and financial behemoths like Visa in August. And email nuisances, spam and phishing, were also on the rise. Will it get better in 2006? Not really, say security experts. In fact, the threats may get worse. That’s because just as security systems become more sophisticated, the threats will become more complex and innovative—all in an effort to stay a step ahead.
Here are the security trends to watch for in 2006:
1. Phishing FrenzyPhishing, the practice of sending fraudulent emails to encourage users to divulge personal or financial information, will increasingly target customers of smaller organizations in 2006.
2. Business Worm’s Rise
Before Zotob struck, computer attacks were often directed at home users. But this worm, which exploited a vulnerability in Microsoft’s Windows operating system, affected businesses, marking the rise of Internet criminals focused on financial gain.
3. Insider ThreatMany of the data leaks in 2005 may have stemmed from poor security measures. And while companies spend millions securing their networks from intruders, they often ignore one of the most likely sources of leaks: insiders or company executives who can inadvertently or deliberately leak information.
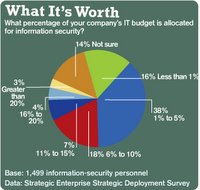
4. Increasing Network ControlThe threat of crooked insiders and more stringent compliance regulations will force companies to implement identity-driven networks that control who uses a network. Driving the change is legislation like Sarbanes-Oxley, which calls for specific security measures and complete visibility into network users, devices, addresses, policies, and activity.
5. Wireless Security FocusHackers are finding it increasingly easy to steal information from devices that contain people’s private data, as a growing number have wireless capabilities, said security experts. Wireless technologies like Wi-Fi may be more widespread, but many users are still ignorant about the security measures they must use on these networks to keep hackers at bay. Security experts see 2006 as the year when threats on wireless networks will come of age.
6.Increased Security LegislationOver the last two years, a number of states have enacted laws similar to one in California requiring companies to disclose security breaches to protect state residents from identify theft. In 2006, a federal law along these lines is a strong possibility, security experts said.
7. Voice Spam BeginsThe popularity of Skype and VoIP will lead to new forms of spam attacks next year, security experts predict. As VoIP applications become more widely used, there will be a rise in voice spam.
8. Selling to SMBsOf course, all these new threats can mean new business for security companies. Traditionally, security companies have focused on selling their products to bigger players as large organizations have big IT budgets that will let them spend on securing their networks. But as smaller firms become the targets of security attacks, security startups will pay more attention to them
CATEGORIES : 1future, 1predictions, 1trends













 Add feed to RSS/XML reader
Add feed to RSS/XML reader Add to My Yahoo!
Add to My Yahoo! Add to NewsGator
Add to NewsGator Add feed to My MSN
Add feed to My MSN Add feed to Bloglines
Add feed to Bloglines Add feed to Rojo
Add feed to Rojo