We have been on the Network Access Control bandwaggon for some time now on this site. Now some heavyweight analysts are "weighing in". Infonetics published some sobering forecasts today. It looks like 2006 is the year that NAC "comes of age", growing from $323M in 2005 to $1.3Bn in 2006.
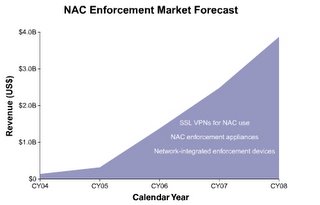
Worldwide manufacturer revenue for NAC enforcement will grow 1,101%, from $323 million to $3.9 billion between 2005 and 2008, according to Infonetics Research’s latest report "
Enforcing Network Access Control". Network access control, or NAC, is considered the holy grail of network security, as it is an intelligent network infrastructure that can identify users, identify and do integrity checks on the computers they are using, and then grant them access to specific locations and/or resources and set policies based on user and machine identity.
There are three main components in most NAC solutions: clients, enforcement, and backend. Infonetics’ report focuses on the enforcement market, including network integrated NAC enforcement devices, NAC enforcement appliances, and SSL VPNs for NAC enforcement. “By far the largest portion of NAC enforcement revenue between now and 2008 comes from network-integrated enforcement devices, but the biggest change is in NAC enforcement appliances, whose share of the market nearly triples between 2005 and 2008,” said Jeff Wilson, principal analyst at Infonetics Research and author of the report.

Three big guns loom large in the burgeoning NAC market: Cisco, Microsoft, and the Trusted Computing Group. The first two are developing their own NAC-like solutions and the third is an independent consortium working on standard implementations for NAC. In addition, there are many companies focused on building NAC solutions, with the NAC enforcement appliance market being a hot area of startup activity.
Report Highlights- Cisco’s NAC solution is the most recognized brand of the three main NAC solutions, followed by Microsoft’s NAP, and then the Trusted Computing Group’s Trusted Network Connect solution in distant third
- The NAC enforcement appliances segment will grow dramatically starting in 2006, growing 3,062% between 2005 and 2008, and will be a volatile space over the next three years, with significant consolidation in the market
- Network integrated NAC enforcement devices will grow almost a thousand percent between 2005 and 2008, and SSL VPNs for NAC enforcement will grow 798%
- The most common type of network integrated NAC enforcement device will be an Ethernet switch that supports 802.1x, and is able to talk to NAC clients and policy servers
RELATED TOPICS : Endpoint integrity architectures start to hot up, Cisco 1st out blocks with integrity architecture, Do you know about the Jericho forum?, First TNC products released, More NAC announcements
CATEGORIES : 1nac, 1endpoint security, 1enforcement, 1trends, 1marketstats, 1report, 1analyst








 Add feed to RSS/XML reader
Add feed to RSS/XML reader Add to My Yahoo!
Add to My Yahoo! Add to NewsGator
Add to NewsGator Add feed to My MSN
Add feed to My MSN Add feed to Bloglines
Add feed to Bloglines Add feed to Rojo
Add feed to Rojo