Cryptography enters mainstream
 #162 The nCipher 2005 Cryptography in the Enterprise Survey, which queried a cross-section of 237 security decision-makers at organizations worldwide, reveals that cryptography is no longer a niche technology. To the contrary, cryptography already underpins a wide array of security functions, and espondents indicate that they plan to rapidly expand their use of cryptography in the near future indicating that cryptography is rapidly maturing as a mainstream security tool.
#162 The nCipher 2005 Cryptography in the Enterprise Survey, which queried a cross-section of 237 security decision-makers at organizations worldwide, reveals that cryptography is no longer a niche technology. To the contrary, cryptography already underpins a wide array of security functions, and espondents indicate that they plan to rapidly expand their use of cryptography in the near future indicating that cryptography is rapidly maturing as a mainstream security tool.This expanded use of cryptography will result in an explosion in the number of cryptographic keys, and equally there will be a wider array of policies under which these keys are governed. In order to enforce security policies consistently, manage risk and comply with regulatory requirements, enterprises will need a robust, automated and centralized key management system.
Highlights:
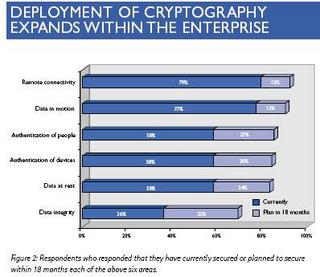
- 74% of respondents are using or plan to use cryptography to underpin at least five different security functions.
- Results show significant future expansion to more than five security functions including: remote connectivity; data-at-rest; authentication of people; authentication of programs, computers or devices; data integrity; and data in motion.
- SSL is already widely used to protect e-commerce transactions over the Internet, with 81% of respondents using SSL for internet-facing servers.
- 46% of respondents said they are using or plan to use 802.1x technologies to authenticate devices, and control user traffic to a protected network and reduce the security vulnerabilities associated with connections
- 25% of respondents have already deployed or plan to deploy TPMs (Trusted Platform Modules) in desktops and laptops within the next two years to encrypt data, protect cryptographic keys and to perform encryption within a secure hardware environment.

0 Comments:
Post a Comment
<< Home