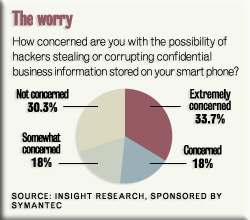
Major concerns about Smartphone security
 Wireless vendors are rolling out a new generation of handheld computers called "smartphones" for corporate users, but many network executives say they won't consider them until the means to manage and secure them are clear.
Wireless vendors are rolling out a new generation of handheld computers called "smartphones" for corporate users, but many network executives say they won't consider them until the means to manage and secure them are clear.For example, Nokia, which uses the Symbian operating system, recently made available the Nokia 9500 Communicator, a handheld with Wi-Fi and cellular support. Nokia says they're the first smartphones it has designed specifically for corporate use. While Nokia created a VPN client, had Symantec develop anti-virus software and Pointsec for encryption for smartphones, users say that's not enough because wireless PDAs must support remote management to meet many corporate security policies.
We have already seen that laptops were the most likely culprits in the recent PnP Microsoft vulnerability - multiply that by 10 times as many mobile smartphones in circulation and you get the idea...It's a classic example of technology getting ahead of security.
And the security worry level has only increased in the past year with the introduction of a slew of varied handheld computers and devices such as the iPod, servers on a data stick, Blackberries, Web-access cell phones, and wireless PDAs and pocket PCs. Not only do all these new devices boast large storage capacities, they also can sustain high data transfer rates thanks to USB, Firewire, Bluetooth, or WiFi connectivity.
Manufacturers of the new smartphones, which began to appear about a year ago, are attempting to entice organizations into buying in bulk as this is where the next growth market is, and you can expect Blackberry , Nokia , Palm and Motorola all competing heavily by using central management capability as the enabling agent for corporate penetration.
We covered the smartphone security issue in a previous blog entry entitled "Major Smartphone worm by 2007 ". Also, InformationWeek has an excellent article on Securing Handhelds which discusses how to deal with the proliferation of mobile and handheld devices from a security perspective.

0 Comments:
Post a Comment
<< Home